By Emily Ashely and Max Broburg

With news of major data breaches making headlines on an almost daily basis, cybersecurity is more important than ever—for both individuals and enterprise. The cybersecurity landscape is changing rapidly. New regulations (i.e. GDPR, California Consumer Privacy Act, etc.) are emerging that companies must comply with, or face hefty penalties. The wave of digital transformation means more connectivity among organizations’ assets, and has led to increasingly complex IT environments (cloud, containers, microservices, IoT, etc.), creating ever-growing attack surfaces and new potential entry points for cyber criminals to strike. This complexity also creates more room for human error, such as misconfigurations, representing huge security risks. Attackers are also getting more sophisticated, leveraging context-aware malware such as the Rakhni Trojan that terrorized companies in 2018. In attempts to help companies solve the myriad of new cybersecurity challenges, vendors are pumping the market with new solutions. In fact, Gartner predicts worldwide information security spending will exceed $124 billion in 2019.
The media landscape clearly reflects what we already know to be true: enterprises today are extremely concerned with cybersecurity challenges and are eager for any and all content that may be helpful. To get a more detailed understanding of how cybersecurity is being covered in technology and business publications, we performed a three-month audit.
In a three-month media audit utilizing TechNews, Meltwater and Google News, we searched for reporters and publications covering cybersecurity from Oct. 10, 2018 to Jan. 10, 2019. We then filtered through the publications to include only U.S.-based business and trade outlets, resulting in 6,697 pieces of unique coverage. From these results, we determined the publications and individual reporters/editors covering cybersecurity most frequently.
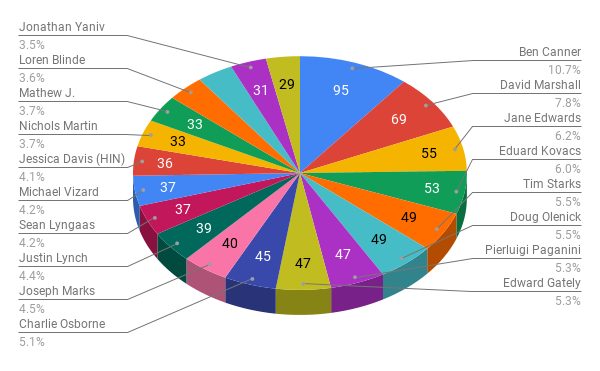
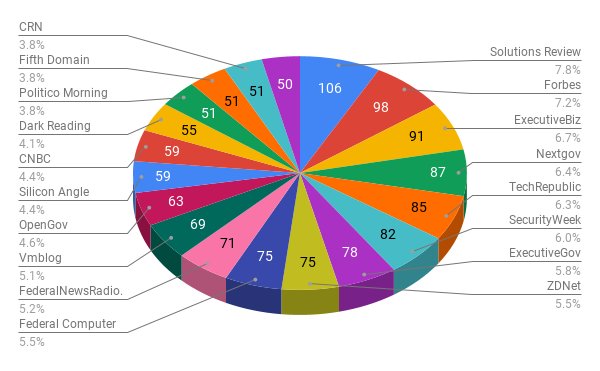
The results of the top publications covering cybersecurity are a healthy mix of security trades (Solutions Review, SecurityWeek, Dark Reading and Information Security Buzz), top tier business publications (Forbes and CNBC), prominent general tech outlets (TechRepublic and SiliconANGLE) and outlets focusing more on government tech and security (ExecutiveBiz, Nextgov, Politico Morning Cybersecurity and Fifth Domain). Given our audit period spanned the federal government shutdown, during which we saw an onslaught of stories pointing out both physical and cybersecurity risks, it’s possible the appearance of these government tech focused publications in our top 20 results are a bit of an anomaly—but we suspect the results would be fairly consistent even looking at a different time period, as concern around cybersecurity of U.S. government organizations, cyber threats from nation-states and election meddling is persistent.
Speaking of the shutdown, this was a common topic among cybersecurity news stories across trade, business and tech publications as well. Because of its far-reaching implications—potentially impacting every American citizen, business and government organization—stories were not confined to a single audience segment.
Other major trends and stories we saw explored in depth include data privacy regulations and compliance, the growing importance of artificial intelligence and machine learning in cybersecurity, nation-state sponsored cyberattacks, cryptomining and cryptojacking, cloud security and more. Being able to speak knowledgably on these key trends and offering unique points of view is an essential strategy for garnering media coverage.
Coverage of major data breaches constitutes a sizeable portion of overall cybersecurity coverage. Publications are quick to share the news when the likes of Marriott, NASA, Nordstrom or Google+ suffers a breach. For cybersecurity experts, these incidents represent an opportunity to share commentary (advice, analysis, criticism, etc.) with reporters and editors likely to cover the news in hopes of their commentary appearing in their stories—but you need to be quick on the draw. Most publications post coverage of a breach within hours of the story first breaking.
Funding news is also common across trades and business publications, as there is no shortage of cybersecurity startups aiming to solve new pain points. Major product announcements can also earn coverage, although to a lesser extent—likely due to the extremely crowded marketplace where it’s hard to differentiate capabilities.
Unlike other industries where strong customer case studies and success stories can garner media coverage, opportunities for cybersecurity case studies are few and far between. Understandably so, since companies are reluctant to expose the mechanics of their cyber defenses or tout their strength, for fear of inviting attackers to target their networks.
While there are certainly challenges to penetrating the cybersecurity landscape, one type of content is almost sure to gain coverage: reports. Cybersecurity reporters and editors are hungry for new statistics and figures illustrating the current state of cybersecurity—be it number of breaches, new vulnerabilities, common causes of breaches, insider threats, the list goes on. Even better, the media is happy to cover these types of reports year after year to illustrate key trends and shifts in the industry over time.
Cybersecurity is perhaps one of the most rapidly changing industries. It’s a three-legged race between digital evolution, which is necessary for companies to innovate and remain competitive, but also creates new potential holes in security; adversaries who are constantly developing more advanced methods of attack; and cybersecurity solutions providers looking to address new vulnerabilities. The good news is, with such a dynamic and multi-faceted issue, there are always new opportunities to share insightful commentary on evolving trends.
Don’t forget to subscribe to our newsletter to get our content and other updates straight to your email as soon as it’s posted!